How to react to a ransomware attack

Disclaimer : some sensitive information related to the analysis of the attack and the remediation was voluntarily omitted to preserve the anonymity of the customer.
It was just a typical day at the office. While everyone was going about their business, a user reported a problem accessing his work files on the internal channel dedicated to infrastructure problems. Soon, other users reported the same problem: locked files next to a text document demanding a ransom. As the system administrator checked the file server, he could see the directories locking up before his eyes. Users’ work files would soon no longer be accessible.
Less than an hour later, the cell phone rings. Our expert instinctively suspects that something is wrong, but he has no idea that he is dealing with a ransomware attack. A crisis team is immediately set up with the client team, and the first decision is to cut off access to the remote working platform. However, the attack continues.
The Revolve team then recommends cutting the VPN link between the on-premises and AWS, and it is the right choice: the attack is stopped. Now it’s time to assess the damage, investigate and find a way to restore access to the files.
Ransomware: identifying attack tools
After investigation, it seems that the hacker managed to connect to a server located on-premises, by exploiting the RDP flaw « Bluekeep », which dates from 2019 (for more info about the exploitation of this flaw, see this video in particular). He then launched a cryptolocker. On the servers where the attack was conducted, the following tools were found:
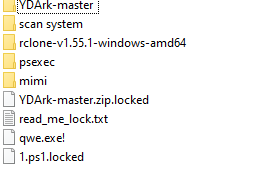
We have found multiple tools that are used in attacks, such as:
- Mimikatz: to read in memory the credentials
- Rclone : to synchronize files to a cloud storage space
- psexec : tool for remote process execution
- xDedic : tool to exploit the RDP protocol
Some of these tools can be easily found online, for less than 10 dollars.
By scanning the servers, the attacker was only able to find the servers that were in the same network as the on-premises RDP server; thanks to the security groups (which define the authorized flows), however, he was not able to see or access the instances present on AWS.
Despite the rapid responsiveness of the crisis team, a certain amount of data was encrypted. The attacker used Rclone to synchronize data between the local server and a remote storage service.
Data restoration and return to normal
One of the first actions taken was to identify the account used by the attacker. The Revolve team was then able to reset the account’s password, and then connect to it. This is how we were able to identify the tools used for the attack, as well as the command line of the crypto tool, and recover the encryption key. It’s not always that simple: here we were lucky enough to deal with an attacker who just used « off-the-shelf tools ».
The team was able to restore the backups set up on AWS. Because the company had migrated to AWS some time ago, virtually no data was lost.
The data was restored within hours using the file server backup (AWS windows FSX server), but also using Microsoft snapshots. A filename recovery script was used to recover and delete all locked files.
How to prevent ransomware attacks
What actions can be taken afterwards to protect against new attacks?
In this particular case, one of the first measures was to stop the RDP servers, which however blocks the possibility of a post mortem analysis. This is an important point to emphasize, in case of an attack, teams must make a strategic choice.
They can either limit the impact as much as possible and shut down everything, or they can leave themselves the possibility of finding the attacker, and therefore protect the evidence and logs to a minimum, which requires more expertise and puts the systel targeted by the attacks at risk for longer. The course of action to be taken, according to the different possible attack scenarios and the associated risk levels, must be decided by the organization and communicated to everyone upstream. Once the incident occurs, it is often very difficult, and too late, to arbitrate calmly.
The passwords of the administrator accounts must also be changed quickly.
Among the good preventive practices, we can also mention :
- Regular and automated backup of servers
- An anti-virus installed and up to date
- Regular patching of servers (just think of the proliferation of zero day vulnerabilities…)
- A dedicated channel, known to users, to report an IT incident, ideally with an on-call service outside working hours
- Automated disconnection of administrator accounts, and of machines on which administrators may be likely to connect
- Limiting the lifetime of passwords and using strong passwords
- Implementing dual SAML and MFA authentication to access cloud services (Appstream, AWS Console, etc)
- Network segmentation: different VPCs and subnets, use of security groups, so as to be able to quickly isolate the impacted part
- The definition of an encryption strategy, to protect your most sensitive data
- The use of an internet proxy to filter and trace accesses from machines to the internet
- Do not expose critical ports such as RDP on the Internet or at least filter the IPs authorized to connect to them, and if there is exposure, special attention must be paid to updates
In this case, the attacker was able to exploit a series of small flaws. This is often the case, a set of small security flaws, which taken individually do not seem to have any consequences. An open port, an unpatched server, an unclosed session… these flaws, when put together, contribute to the fact that the hacker can get close to his target, with consequences that can be heavy for the company.
Individually, preventive actions are also easy to implement: use strong passwords, patch servers, configure Windows to automatically close sessions, etc. The fight for security is not necessarily expensive, nor is it a losing battle against technologically superior hackers. It is necessary to start with the basics, thus reducing the attack surface.
Any simple preventive action should be taken, and what can be automated should be.







